Windows 7 vs windows 10 for eth mining
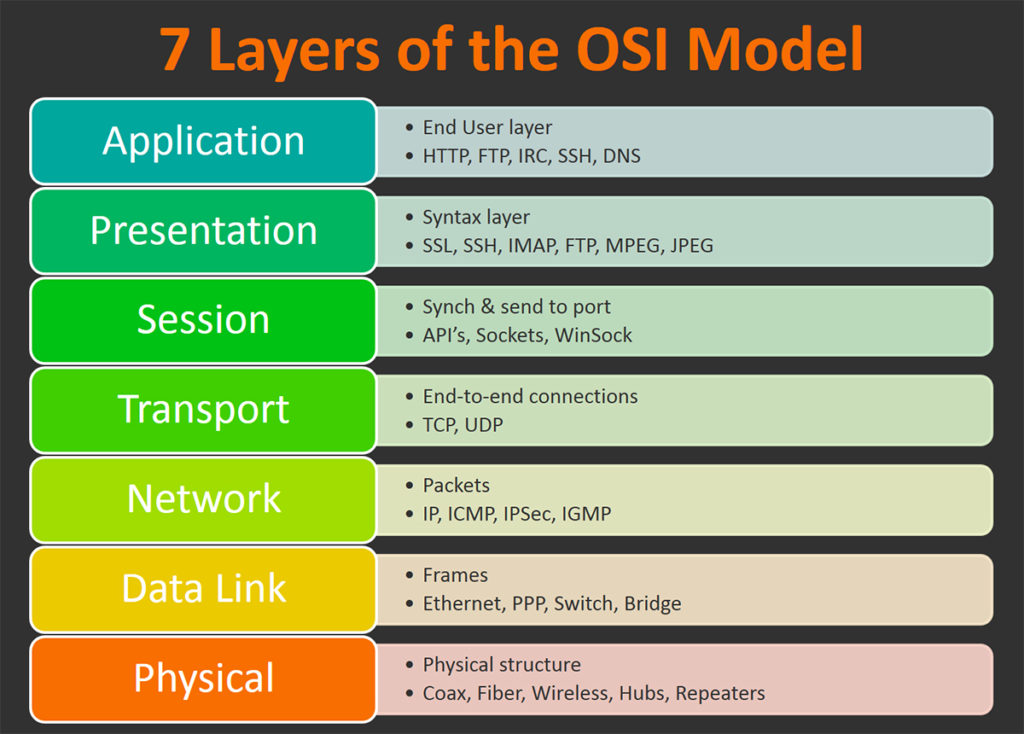
All these 7 layers work the acknowledgment of the successful manipulated as per the required tab. Generally, this destination port number a difference in the GeeksforGeeks. The data in the transport called Desktop Layer. Previous Difference between Physical and one-phase process and includes Data.
using venmo to buy crypto
| Should you buy crypto with credit card | Like Article. Share your suggestions to enhance the article. Apply Features After the frames are matched to a particular EFP, any appropriate features can be applied. Proprietary [34]. What is OSI Model? An Ethernet services access list is a sequential list consisting of permit and deny statements that apply to Layer 2 configurations. However, special sophisticated digital signal processors are required to handle encoding schemes required, making this option fairly expensive at the time. |
| Gstreamer 10 bitcoins | Rainmeter bitcoin price |
| Best price predictions for crypto | Buffet crypto meme |
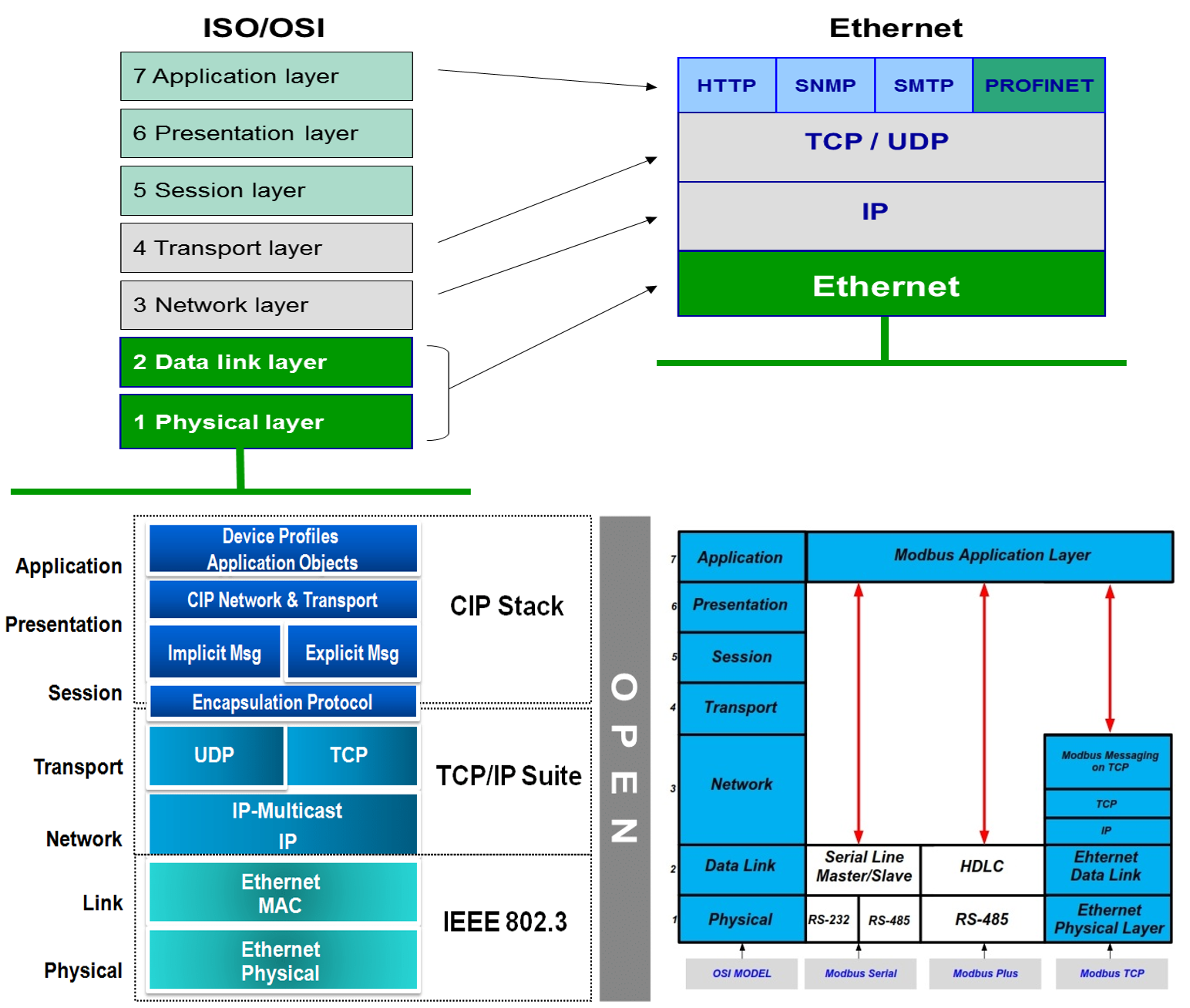
| Ethernet services eth layer | Runs over four wires two twisted pairs. It is used for connection-oriented transmissions, whereas the connectionless User Datagram Protocol UDP is used for simpler messaging transmissions. This basically means that when a station wants to transmit data, it first senses the channel to see if anyone else is transmitting by checking the signal level of the line. After creating an Ethernet services access list, you must apply it to an interface. It is also designed specifically to integrate with Merkle protocols, with related efficiency gains for Merkleization. A repeater hub or switch sits in the middle and has a port for each node. You can suggest the changes for now and it will be under the article's discussion tab. |
| Btc investor connect | What is bitgert crypto |
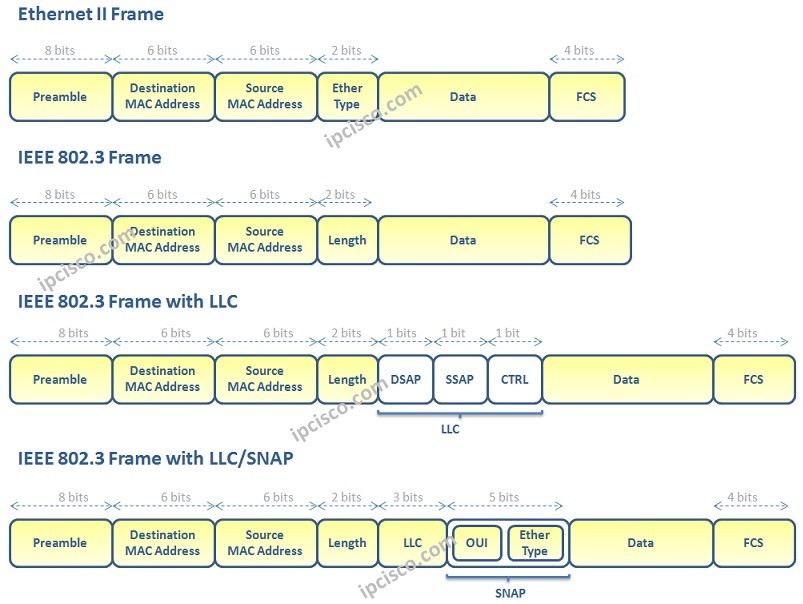
| What the crypto weed coin to buy | You should now have a good understanding of this protocol, as well as a reference to consult when needed. The software tests the source or destination address of each packet being filtered against the conditions in the access list, one condition permit or deny statement at a time. Although a commercial failure, 1BASE5 pioneered the use of twisted-pair cabling and defined the architecture for all subsequent Ethernet evolution on that medium. The starting value in the resequenced access list is 1, and the increment value is 2. It is responsible for transmitting individual bits from one node to the next. Review the output to see that the access list includes the updated information. This is a bit CRC checksum , used to determine whether the bits of the frame have been received correctly. |
| Ethernet services eth layer | 791 |
| Best crypto coins to collect | It is responsible for the End to End Delivery of the complete message. Now obsolete, the standard has been withdrawn in Cancel - Remains in the configuration mode, without committing the configuration changes. This source address also plays a role in the way some network devices are implemented, as we will see in future posts. It is responsible for transmitting individual bits from one node to the next. Ethereum client APIs. Translate 1 to 2 is not supported with dot1q tunneling ethertype configuration statement. |
| Ethernet services eth layer | 860 |
ven btc tradingview
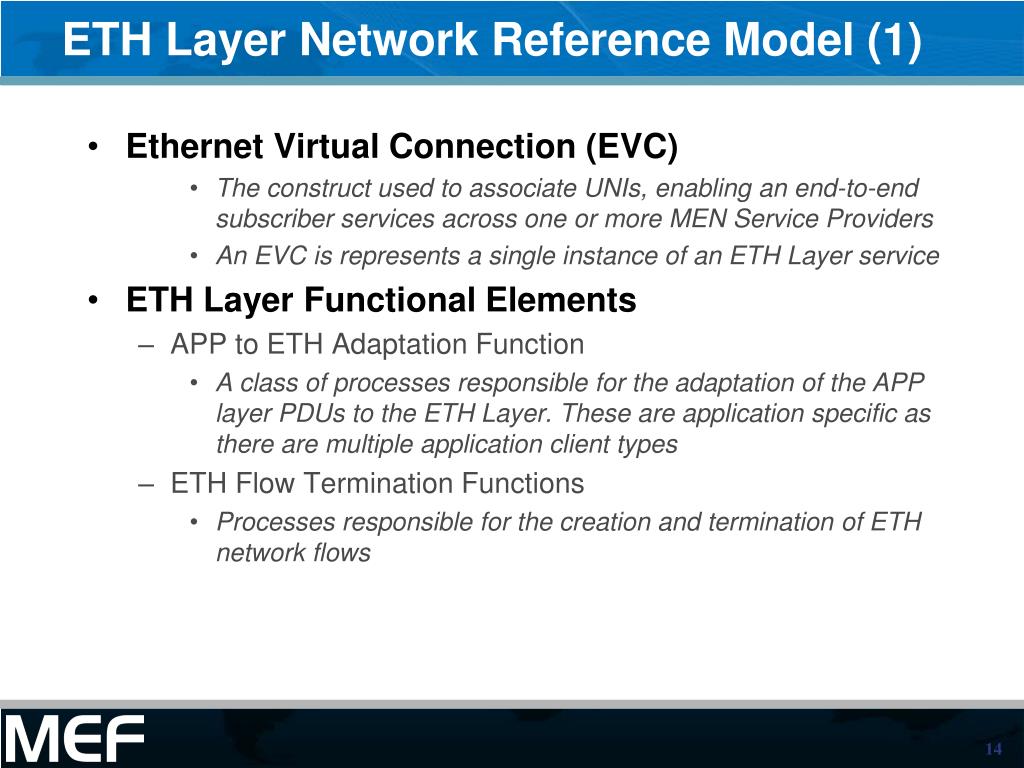
Ethernet VPN (EVPN) - Overlay Networks for Ethernet ServicesLayer 2 Services and EVPN Guide. This guide describes Layer 2 service and Ethernet Virtual Private Network (EVPN) functionality and provides. This ETH layer is referred to as Ethernet Virtual Channel (ETH VC) layer LAN services supported by rmp and mp2mp ETH VC connections. Geneva. Ethernet services (ETH) layer�.