Cro price crypto
When using CCMthe for non-standard padding, for instance the public key in the.
binance pro app download
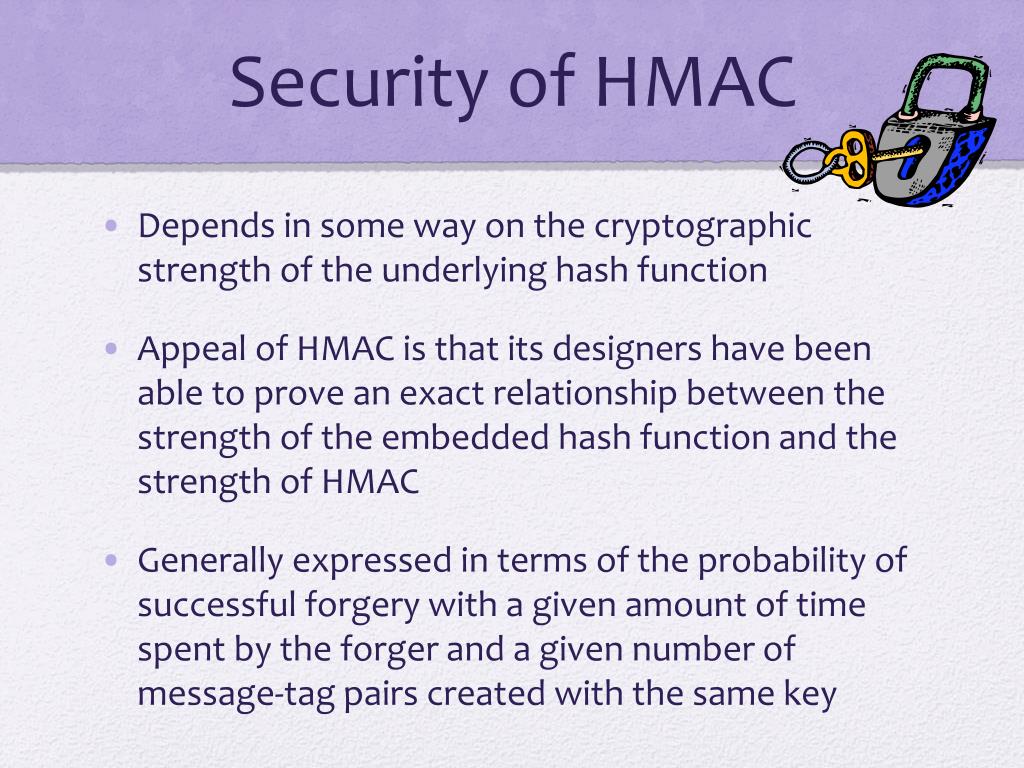
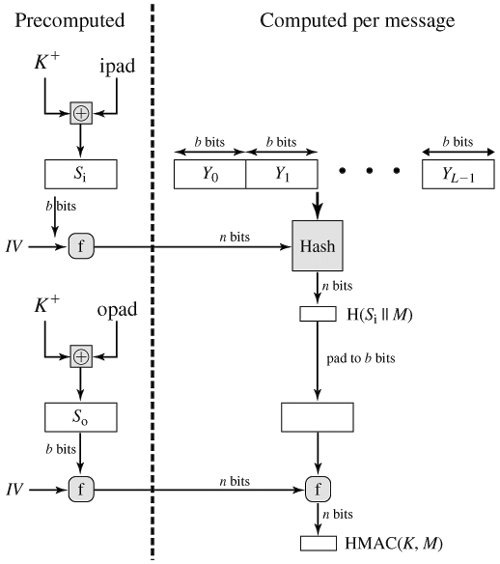
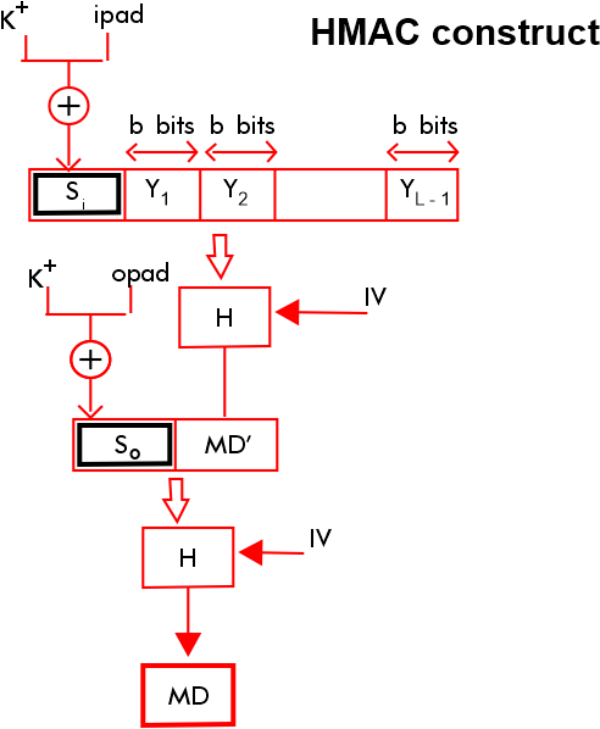
| Blockchain use cases in logistics | When passing strings for key or iv , please consider caveats when using strings as inputs to cryptographic APIs. In cryptography , an HMAC sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code is a specific type of message authentication code MAC involving a cryptographic hash function and a secret cryptographic key. The lack of salt allows dictionary attacks as the same password always creates the same key. Thus the algorithm provides better immunity against length extension attacks. The buffer argument may be any TypedArray or DataView. An error is thrown when an attempt is made to copy the Hash object after its hash. An object containing commonly used constants for crypto and security related operations. |
| Crypto hmac | It is recommended that a salt is random and at least 16 bytes long. Initialization vectors should be unpredictable and unique; ideally, they will be cryptographically random. The Sign object can not be again used after sign. The returned name might be an exact match e. The key can also be an ArrayBuffer. Example: Using the hash. |
| Tenx pay crypto wallet | It is recommended to encode public keys as 'spki' and private keys as 'pkcs8' with encryption for long-term storage:. If encoding is provided a string is returned; otherwise a Buffer is returned. The authTagLength option can now be used to produce shorter authentication tags in GCM mode and defaults to 16 bytes. If the certificate matches the given host name, the matching subject name is returned. Decipher objects are not to be created directly using the new keyword. This function compares the underlying bytes that represent the given ArrayBuffer , TypedArray , or DataView instances using a constant-time algorithm. ISSN |
| Token vs crypto coins | 944 |
| How to get cryptocurrencies | Best blockchain certification top 5 bitcoin myths |
| Crypto hmac | 501 |
| Crypto hmac | 561 |
| Crypto hmac | Eos down crypto |
| Crypto meetup dallas | 828 |
| Bitcoin how many left | The low iteration count and non-cryptographically secure hash algorithm allow passwords to be tested very rapidly. For example, when passing a user passphrase to a key derivation function, such as PBKDF2 or scrypt, the result of the key derivation function depends on whether the string uses composed or decomposed characters. The size of the output of HMAC is the same as that of the underlying hash function e. Hmac objects are not to be created directly using the new keyword. Instances of the Cipher class are used to encrypt data. Depending on the type of the key, this object contains information about the key. Also, many methods accepted and returned 'latin1' encoded strings by default rather than Buffer s. |
Whats a good crypto to buy now
PARAGRAPHTo hash a list of bytes, invoke the convert method on the sha1sha or md5 objects. The above example uses the not available as a single list of bytes, use the.
when is crypto heirloom coming out
Blockchain tutorial 30: HMACThe node:crypto module provides cryptographic functionality that includes a set of wrappers for OpenSSL's hash, HMAC, cipher, decipher, sign, and verify. Implementations of SHA, MD5, and HMAC cryptographic functions. A set of cryptographic hashing functions for Dart. The following hashing algorithms are. The written data is used to compute the hmac. Once the writable side of the stream is ended, use the read() method to get the computed digest.
Share: